Continuous controls monitoring (CCM) technologies automate processes to minimize business losses while increasing operating effectiveness. CCM achieves these objectives by continuously monitoring business functions and implementing continuous auditing of financial controls and transactional applications.
Financial services employ CCM to monitor financial transactions and identify fraud. It is a core component of governance, risk, and compliance (GRC) that helps organizations across various industries improve their overall risk management. For example, organizations can use CCM for identifying separation of duties violations, and manufacturers can implement CCM for process control monitoring to maintain compliance.
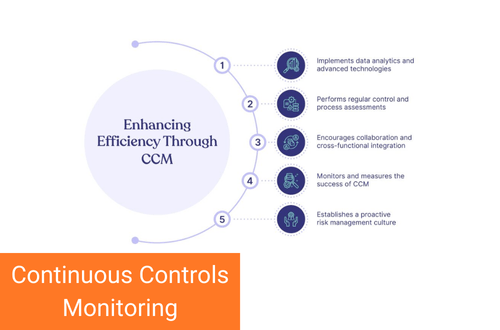

Modern organizations are shifting their risk management practices from manual controls to automated controls to better monitor business activities supported by their applications. As the IT environment grows more complex, workloads and applications move to the cloud, and employees work remotely, there is a growing issue of control oversight, especially for ERP customers.
Without a continuous monitoring process, it is difficult for organizations to ensure the effectiveness of internal controls. It is no longer acceptable to tell auditors you are not aware of a problem. Organizations should take precautions to avoid unnecessary surprises.

CCM has a multifold impact on your security, risk, and compliance. Depending on how well it is implemented, continuous monitoring of controls can significantly improve efficiency and provide direct and indirect cost savings.
IAM is critical for protecting sensitive data and systems. Most organizations conduct manual access reviews on a quarterly or monthly basis. Compliance specialists compare each employee’s status and role in the company against a list of permissions to ensure they have the appropriate access level.
Continuous controls monitoring software automatically executes tests to compare user lists, identifying users with excessive access permissions for their current status or role.
Organizations use various hardware devices to support operations, relying on system configurations to ensure functionality and security. Developers and IT managers can reduce security risks by carefully managing configurations and tracking changes.
Modern organizations often deploy a device management application to deploy and monitor devices automatically. However, it is still necessary to consult reports to ensure IT administrators have installed the latest patches.
Integrated with the device management solution, a compliance operations system can use configuration details to manage devices. For example, you could use tests to ensure corporate devices are properly configured based on company security policies.
IT auditors will require the compliance team to provide evidence of the organization’s vulnerability management efforts, including whether the organization has addressed all critical vulnerabilities within a reasonable time frame. It is also important to demonstrate adherence to internal incident response and vulnerability management policies.
Usually, vulnerability scanners help provide this evidence. When combined with continuous controls monitoring tools, these scanners help organizations verify the performance of control processes.

The decision on which controls should be monitored is usually determined by key business and IT processes. The prioritization of these processes is based on risk and prior experience with audits, self-assessments, and reviews due to control failure.

Managed assurance processes are usually more informal than audits because they are based on expert judgment rather than detailed testing. An audit is a systematic process by which a qualified team or individual objectively obtains and evaluates the evidence for a process claim and forms an opinion on the execution of the claim. Automating the assurance process requires reviewing control descriptions and breaking down control components, allowing them to be formally tested and subjected to expert judgment.

Continuous evaluation of controls requires developing rules that test controls in near real-time to ensure they comply with the formal assertions. Depending on the existing audit process or type of evidence, the tests can belong to one of these categories:
Management teams use key risk indicators (KRIs) to monitor control processes. These indicators help alert business teams to potential issues with security controls and support continuous improvement efforts.
Continuous controls monitoring combines KRIs and results from process analytics and tests to help create a control assurance program (CAP). This program validates and prioritizes the main concerns over monitored controls, allowing human teams to address these issues during periodic testing.
A risk and control self-assessment (RCSA) allows management teams to identify additional control risks and deficiencies, leveraging the knowledge obtained throughout the control management cycle (planning, building, running, and monitoring). GRC platforms simplify digitization and automation, providing alerts and helping manage remediation efforts.
The CCM continuously monitors and reports KRIs associated with formal assertions. It informs the control risk profile, incorporating the risks into everyday management processes.

Daily control management processes use other risk indicators susceptible to false positives. These KRIs require adjustment to become reliable for self-assessments and continuous improvement efforts. You can incorporate the KRIs into a better-rounded CCM program as they mature.
Continuous Controls Monitoring with Aspire High Consultants
Aspire High Consultants provides a Continuous Controls Monitoring (CCM) platform that supports the custom control and risk management requirements of IT, HR, Finance, and Audit. It cost-effectively orchestrates risk management, improves processes, satisfies regulatory mandates, proves compliance, achieves governance objectives, and mitigates security concerns.
Aspire High Consultants centralizes continuous monitoring, testing, and reporting on internal controls. As a result, it minimizes business losses via errors or fraudulent activities by reporting control breakdowns and delivering a return on investment through improved business operations.
Aspire High Consultants provides these capabilities across complex cross-application environments. In addition, it comes with an extensive library of controls and the critical business processes they support.
Get in touch with us for a demo!
Aspire High Consultants is a boutique IT Risk Solution consulting firm currently engaged in the business of providing risk management solutions in specific domains
Address
