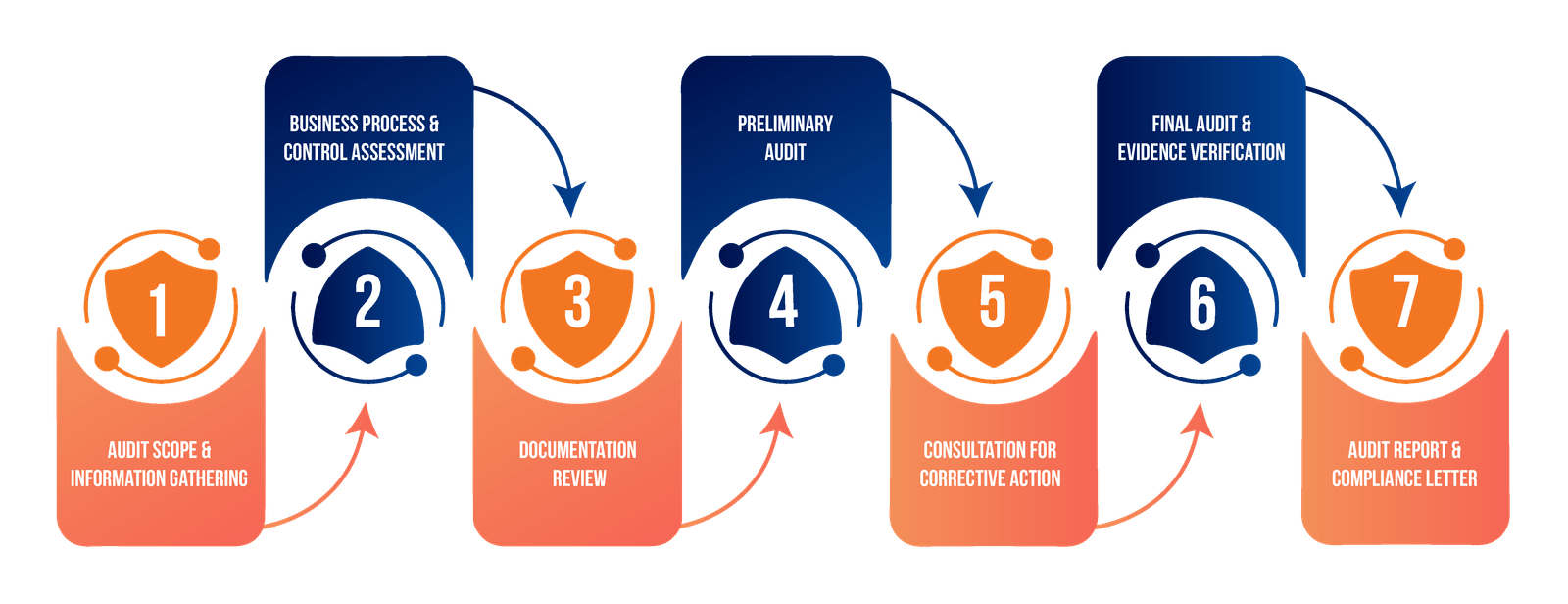
We begin with a thorough review of your existing access management infrastructure to establish a clear baseline. This phase involves understanding your organization's specific business processes and compliance requirements, while identifying all systems and applications that require evaluation

Our team meticulously documents your current user roles and their associated permissions across all systems. We create a detailed matrix of access rights that provides visibility into your entire access structure while identifying any potential Segregation of Duties conflicts that could pose risks.

We conduct an extensive evaluation of all access rights, comparing them against industry best practices and security standards. This includes careful scrutiny of sensitive permission sets and a systematic identification of security vulnerabilities and compliance gaps that need addressing.

Based on our analysis, we develop a comprehensive report containing specific, actionable recommendations for improvement. We provide detailed guidance on necessary access right modifications and create a strategic roadmap that outlines the implementation steps for all recommended changes.
Our team works alongside yours to implement the recommended access control improvements effectively. We provide targeted training to your IT and security teams to ensure smooth adoption of new processes while offering continuous support and consultation throughout the implementation phase.
The duration varies depending on the complexity of your organization’s systems, typically ranging from 2-6 weeks.
Yes, we have expertise in reviewing access controls across various platforms, including cloud and on-premises systems.