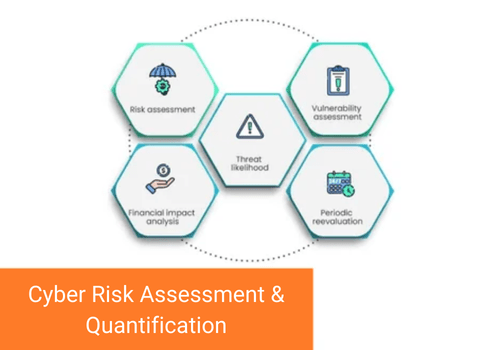
Cyber risk assessment and quantification transforms complex security data into clear financial values. This advanced methodology moves beyond traditional security checklists by calculating the exact financial impact of each digital threat to your business.
Think of it as a financial forecast for your cybersecurity. Just as financial forecasting helps predict revenue and growth, cyber risk quantification helps predict potential losses from cyber threats. We measure factors like:



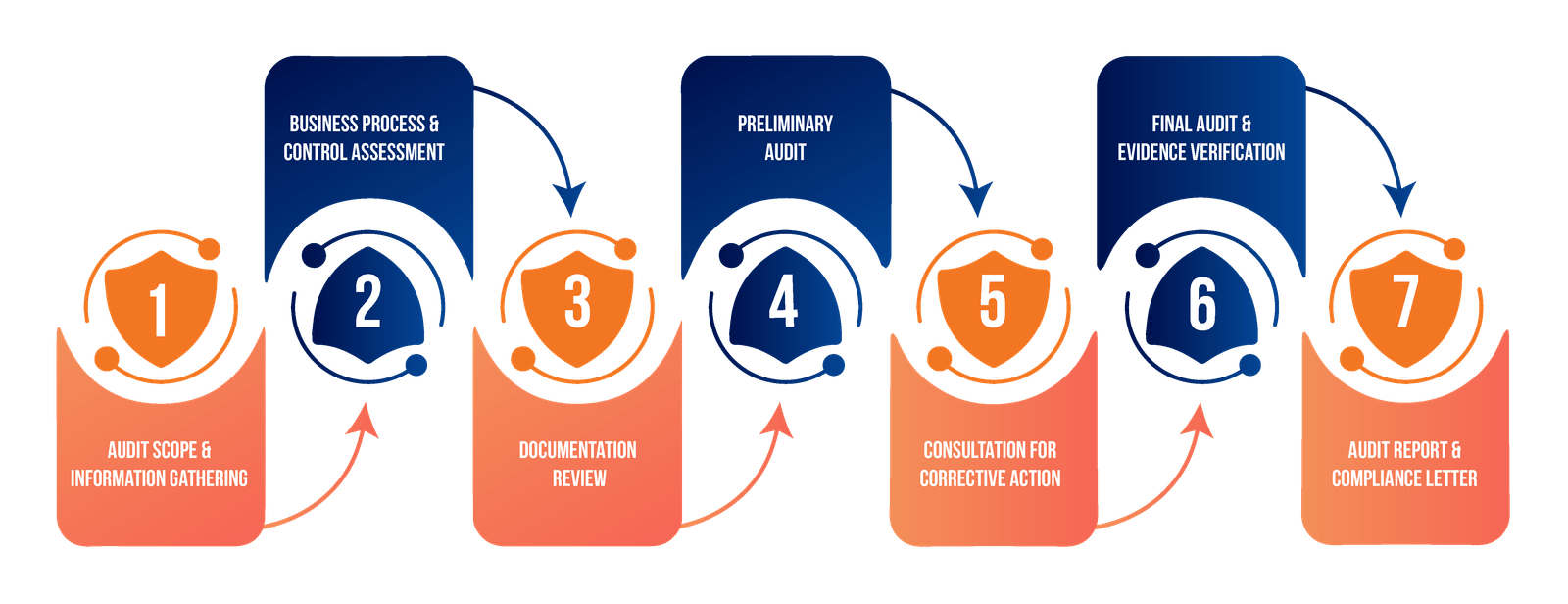
We begin with a thorough discovery phase that includes a comprehensive inventory of your digital assets and their interconnections. Our team conducts detailed business impact analysis to understand critical processes and dependencies. Through targeted stakeholder interviews, we gather insights about your organization's unique challenges and objectives.

Our experts employ sophisticated threat modeling techniques to identify potential attack vectors and scenarios specific to your environment. We conduct thorough vulnerability assessments across your infrastructure, applications, and processes. This phase includes a detailed evaluation of your existing control effectiveness, identifying gaps and opportunities for improvement.

Using advanced financial impact analysis, we translate technical risks into monetary terms your business leaders can understand. Our probability modeling creates realistic estimates of threat likelihood and frequency. We develop comprehensive loss scenarios that consider both direct and indirect costs, helping you understand the full scope of potential impacts.

We deliver an executive summary that clearly communicates key findings and critical insights to leadership. The detailed risk analysis provides in-depth technical information and supporting data for your security team. Our prioritized remediation roadmap gives you a clear path forward, with specific, actionable steps to improve your security posture.