One Stop Solution
SaaS businesses need to inspire confidence and trust about how they manage and establish data security to clock continued growth. And the best way to build such trust is by gaining independent and internationally-recognized accreditations for your security controls.The ISO 2700 certification is one of the most recognized international security standards. It demonstrates your commitment to upholding global best practices in information security and adds to your competitive advantage.The ISO 27001 audit, therefore, is critical to determining whether your organization meets the ISO 27001 requirements.

An ISO 27001 audit comprehensively evaluates an organization’s Information Security Management System (ISMS). It aims to determine whether the ISMS complies with all requirements specified by the standard. An audit analyses the effectiveness of security controls, risk management processes, and overall information security (IS). The main objective is to ensure that the ISMS protects sensitive information, maintains data and systems’ confidentiality and integrity, and assures availability.
The requirements of ISO 27001 audit (internal audit) are described within the standard’s documents. All the requirements come under Clause 9.2 of the ISO 27001 standard. Let’s have a look at the sub-clauses to understand each requirement.
The ISO 27001 standard mandates organizations to undergo internal audits before they present themselves to an accredited external auditor for certification.

ISO 27001 internal audits are executed internally to evaluate whether their ISMS meets the requirements of the standard. The management can designate an internal team (known as an ISO 27001 internal auditor) or contract out the audits to external auditors.
The ISO 27001 internal audit is much like a reconnaissance. It’s the exercise of looking for gaps, non-conformities, and vulnerabilities in the ISMS before the external audit.
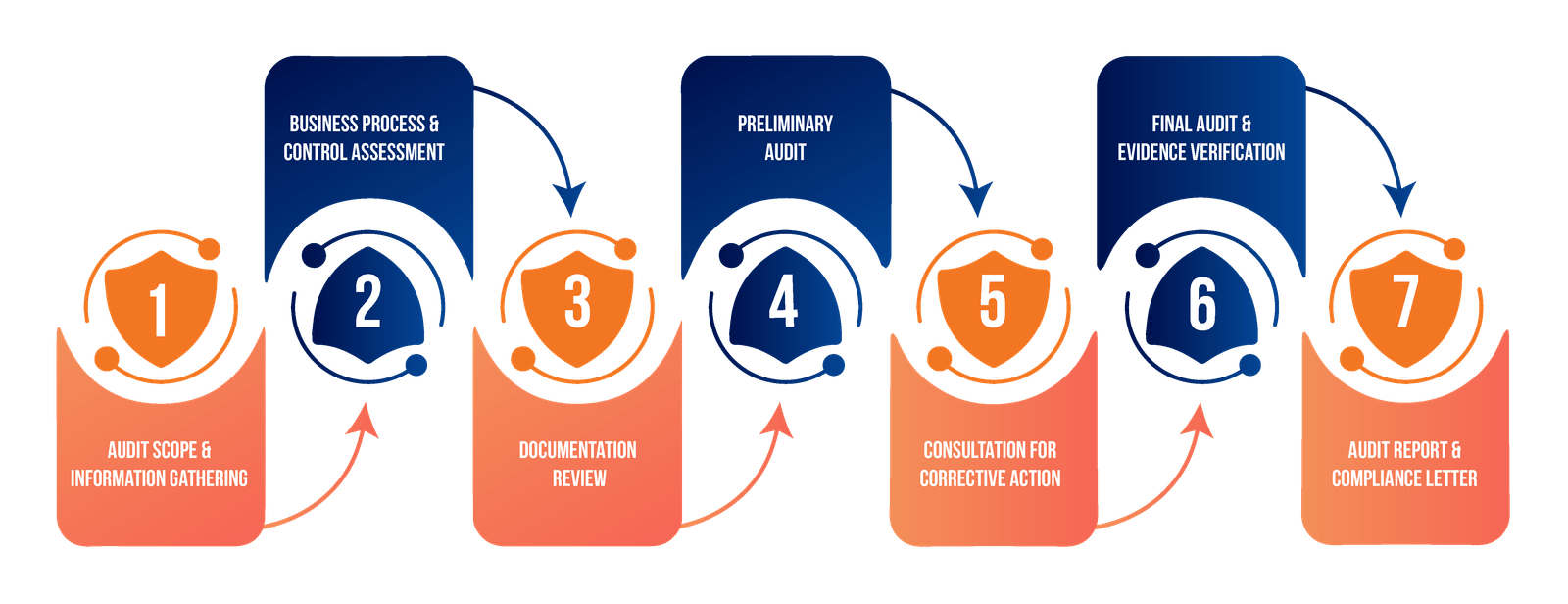
Before we dive into what an internal audit report contains, let’s look at the steps that you should take to get started with the internal audit process.

A brief alignment of your business and security objectives is a must. To do this, ask yourself which service, product, or platform your customers want ISO certified and what are your business-critical audit processes and products

Select which information assets and systems to include in the ISMS in the Scope Statement, and ready the Statement of Applicability (SOA) by detailing which Annex A controls apply to your organization.

Conduct an internal risk assessment of your assets and systems, identify the risks that could impact data confidentiality, integrity, and availability for these, assign a probability of their occurrence, and peg the impact levels (high to low). The risk treatment involves procedures to be taken to decrease the identified risks to an acceptable level.

The ISO 27001 audits are heavy on documentation and require the organization to set up policies and procedures to control and mitigate risks to its ISMS.

Employees are the first line of defense in the event of cyber- attacks, breaches, and hacks. Therefore, employee awareness and certification training play a significant role in the ISO 27001 standards.

Monitor the ISMS, do a gap analysis, remediate, test more, and monitor – this endless cycle can help you strengthen your ISMS. Continual improvement is the name of the game.

Once the internal audit gives a clean chit, organizations are ready to undergo an external audit. The process of the external audit is the same as that of an internal audit, the difference being it leads to certification (or recertification, as the case may be).
The external audits are conducted as follows:

Preparing for ISO 27001 certification involves navigating two integral stages comprising the initial certification audit. Understanding these stages is crucial as they dictate the audit criteria for ISO 27001 and determine certification eligibility.
This phase requires thorough preparation, including defining risk tolerance, ensuring security benchmarks align with partner expectations and legal obligations, and documenting processes and controls per ISO standards. An auditor reviews this documentation to ensure compliance and suggests improvements.
After a positive recommendation from stage 1, an auditor from a certifying body conducts an evidential field review. They confirm alignment between documented procedures from stage 1 and the actual business processes and controls within the Information Security Management System (ISMS). Auditors assess a range of data and assets to verify the effective operation of the ISMS and interview key stakeholders involved in managing security measures.
Successful completion of the stage 2 audit results in ISO 27001 certification for three years. Yearly surveillance audits are then required to maintain continuous compliance. These audits demonstrate that controls function as intended and adhere to the internal audit schedule submitted to the certifying body.
Generally, an external auditor with relevant experience and certification performs the ISO 27001 audit to assess the organization’s compliance with the set standards and requirements by examining the ISMS. The external auditor can be either an individual or a third-party auditor firm that performs ISO 27001 audits.
An internal auditor can also perform the ISO 27001 audit. To perform an audit, they should have completed a specified number of audits and hours of training. However, the final ISO certification is issued by the certification body itself.
There are two phases of the ISO 27001 audit that takes up to 6 months to complete. After the first phase of on-site inspection and documentation audit, the organization needs to work on the correction of non-conformities to get ready for the second phase. Based on the size of the organization and the number of major non-conformities, the time for the Phase 2 audit varies.
So, if you address the non-conformities by implementing your ISMS in an efficient and compliance-driven way, the audit process will take less than 5-6 months.
The Aspire High Consultants Way
Aspire High Consultants compliance automation platform is built to help SaaS firms make confident strides in their security journey. From intelligently mapping and minimizing risks to breaking down the entire process into logical, tactical steps, your compliance experience with Aspire High Consultants is designed to be easy, error-free, and fast.
From defining the scope of your ISMS to setting up robust information security policies, deploying entity-level checks, and implementing InfoSec training programs for employees, Aspire High Consultants does everything for you.