ISO/IEC 27701 is a privacy extension to ISO/IEC 27001, which is an international standard for information security management systems (ISMS). ISO 27701 provides guidance and requirements for establishing, implementing, maintaining, and continually improving a Privacy Information Management System (PIMS). It focuses on enhancing an organization’s ability to protect personal information and comply with privacy regulations. ISO 27701 compliance helps organizations demonstrate a commitment to protecting personal data and respecting individuals’ privacy rights.

ISO/IEC 27701:2019 is a privacy extension to the International Information Security Management Standard, ISO/IEC 27001 (ISO/IEC 27701 Security techniques – Extension to ISO/IEC 27001 and ISO/IEC 27002 for Privacy Information Management – Requirements and Guidelines).
ISO 27701 specifies the requirements for – and provides guidance for establishing, implementing, maintaining and continually improving – a PIMS (Privacy Information Management System).
ISO 27701 is based on the requirements, control objectives and controls of ISO 27001, and includes a set of privacy-specific requirements, controls and control objectives.
This will set the standard for data protection practices and help organisations demonstrate that they have the appropriate control environment in the form of a Privacy Information Management System (PIMS) which integrates with the Information Security Management System (ISMS).
It is applicable to all industries and to organisations of every size, and covers the processing of personal information for all data subjects.

ISO/IEC 27701 is applicable to all types and sizes of organizations, including public and private companies, government entities and not-for-profit organizations who stores, collects or processes Personal Identifiable Information PII such as name, contact, location, IP address etc. It provides guidance for organizations who are responsible for PII processing within an information security management system (ISMS), specifically:
The objectives of ISO 27701 standards are:

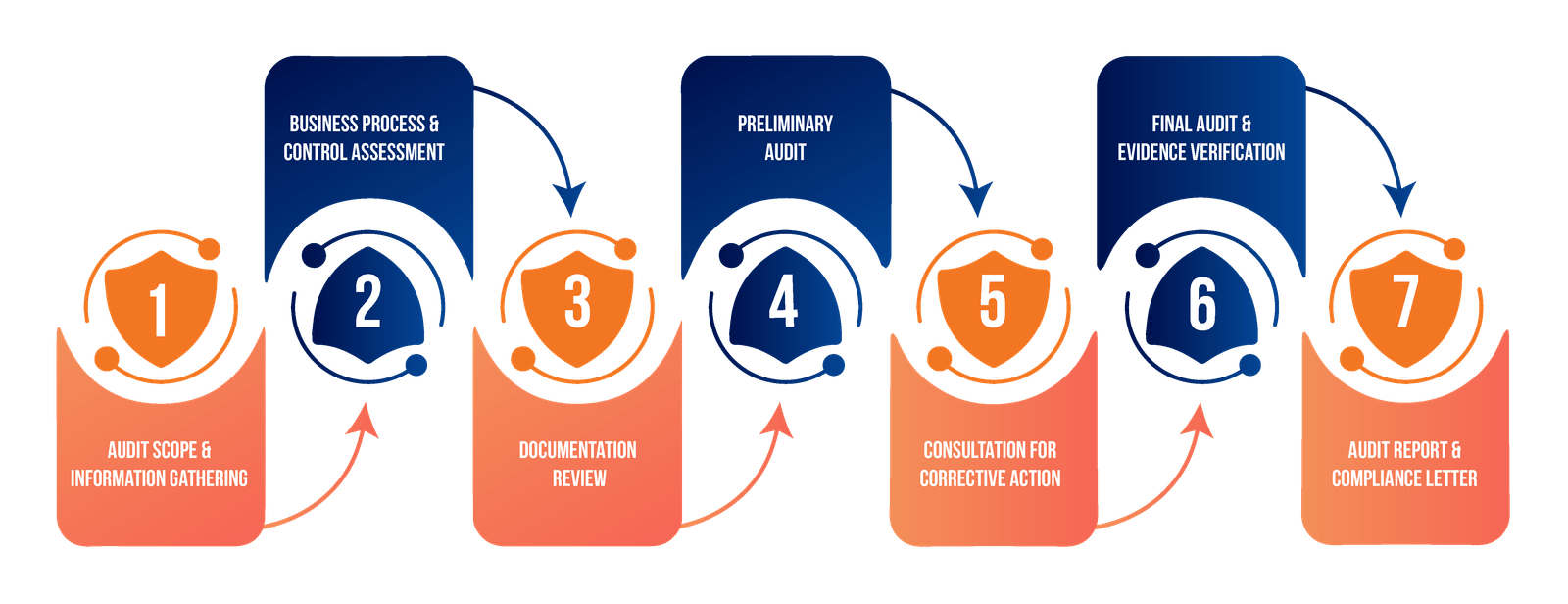
Our approach has been covered in a 5 phases. These include:

Understanding the environment and management’s expectations along with the policies and procedures.

Identify target processes and understand the process flow, risk, information assets and controls pertaining to processes.

Identify controls based of 27701 and prepare the issue and opportunity registers, test the control design and identify deficiencies. Prepare risk mitigation plan and calculate the residual risks.

Perform internal audit and identify the control weaknesses and impact of deficiencies.

Invite certification agency for the certification audit
It’s an important practice that gives organizations visibility into real-world threats to your security. As part of a routine security check, penetration tests allow you to find the gaps in your security before a hacker does by exploiting vulnerabilities and providing steps for remediation.
Our experts will furnish an itemized security evaluation report with legitimate remediation steps to be taken.
Distinguish Security Weaknesses inside your Digital Asset permitting you to proactively remediate any issues that emerge and improve your security act.
Constantly updating Vulnerability Information to stay in touch with the emerging threat landscape.
Receive overview and trend data of all of the current security issues you face in your organisation. All viewable on a Digital Report.
We also assured you that your assessments are executed by qualified experts.
Our group of security specialists holds industry capabilities, for example, CHECK Team Member and Team Leader, CEH, CISA, CISSP, and many more.

Aspire High Consultants is a boutique IT Risk Solution consulting firm currently engaged in the business of providing risk management solutions in specific domains
Address
