IT General Controls (ITGC) is the foundation of a robust IT governance framework, encompassing the policies, procedures, and practices that ensure your organization’s information technology systems operate reliably and effectively. At Aspirehigh Consultant, we specialize in implementing and optimizing these critical controls to protect your IT infrastructure and maintain data integrity.
Our ITGC services cover key areas including access management, change management, system development, and IT operations. We ensure these fundamental controls work together seamlessly to support your business objectives while maintaining security and compliance standards.

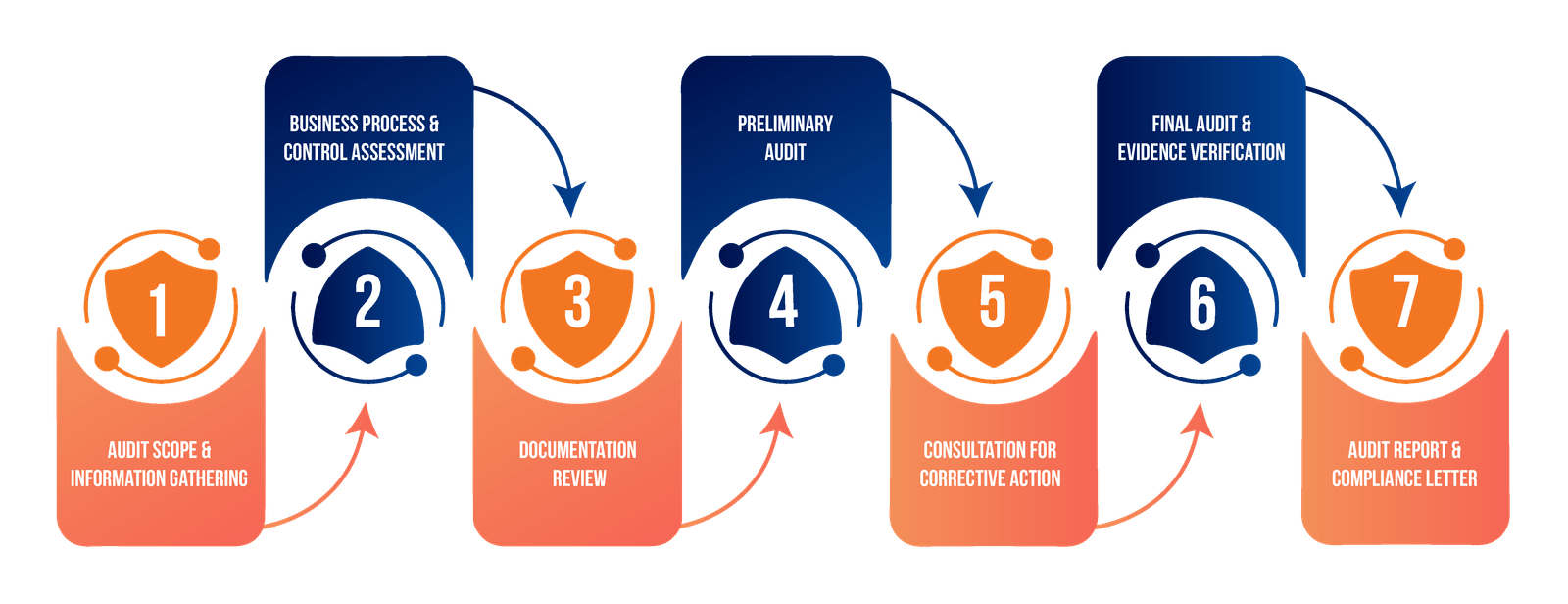
Our ITGC implementation ensures your organization is always prepared for internal and external audits. We maintain detailed documentation and evidence of control effectiveness, simplifying the audit process.