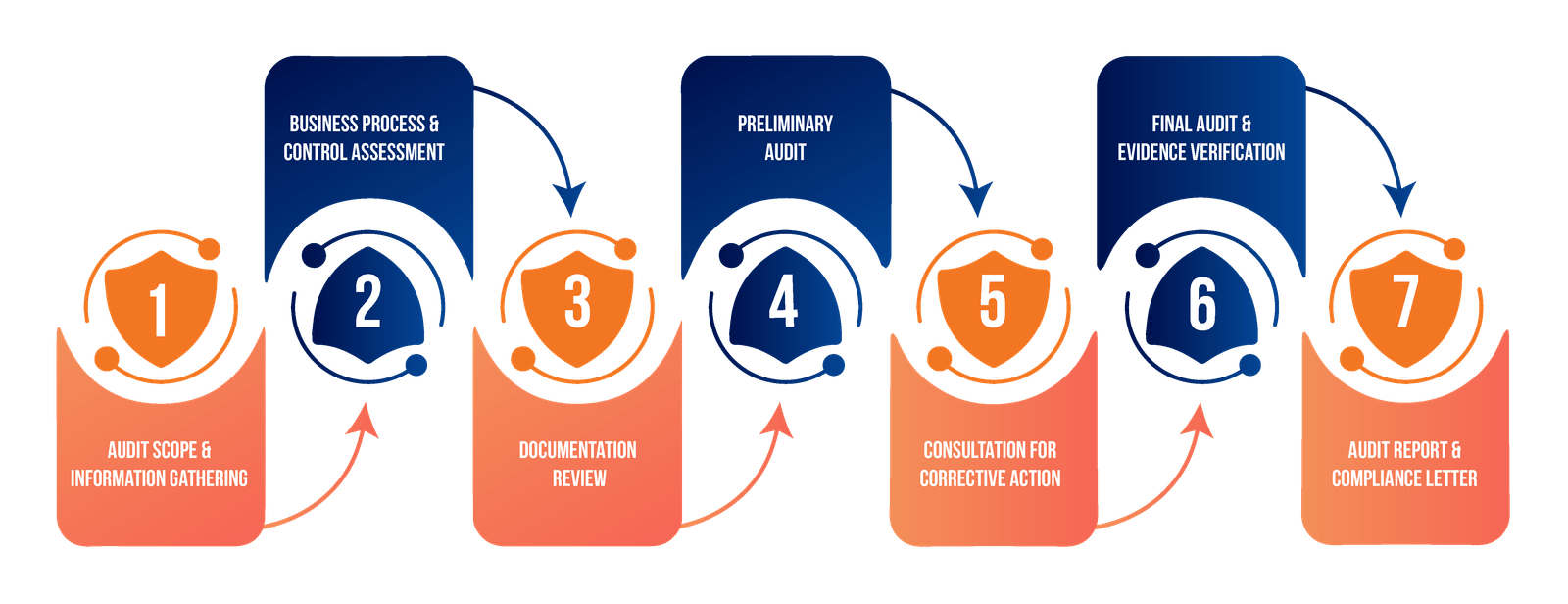
We examine your entire network architecture, including endpoints, servers, cloud services, and security controls.
Understanding potential attack vectors specific to your industry and business model.

Identifying areas where security measures may fall short of requirements or best practices.

Ensuring your network architecture supports both security needs and business operations.