In today’s evolving threat landscape, NIST has emerged as the cornerstone of robust cybersecurity standards across industries. As a trusted federal agency, NIST provides comprehensive protocols and guidelines that shape how public and private sectors protect sensitive data and systems. At Aspirehigh Consultant, we leverage these proven methodologies and recommended practices to strengthen your organization’s security posture through our industry-leading NIST framework implementation services.


NIST (National Institute of Standards and Technology) compliance involves adhering to a set of cybersecurity frameworks, guidelines, and standards designed to protect organizational assets and sensitive information. These frameworks provide structured approaches to:


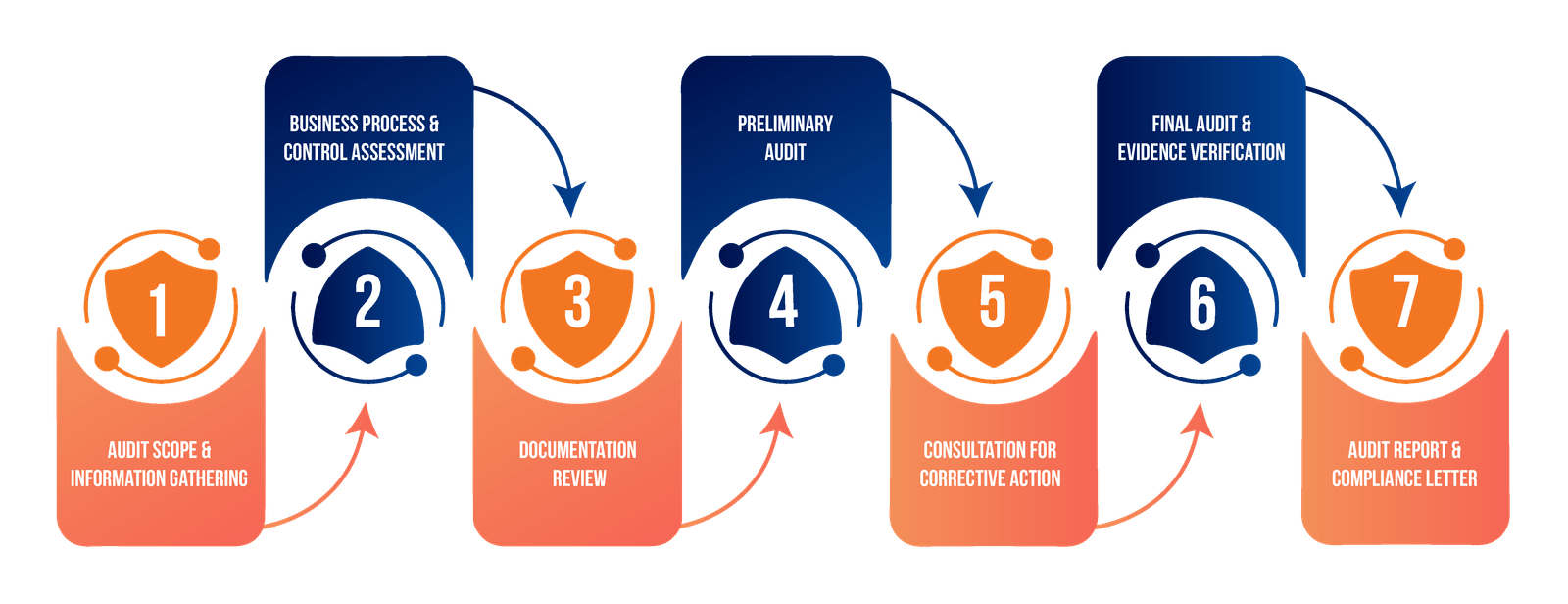
The Assessment Phase involves conducting a thorough gap analysis and security assessments to identify weaknesses in the existing system. This phase also includes risk evaluation and vulnerability scanning to detect potential threats. A review of the current security posture is carried out to understand where the organization stands in terms of compliance and protection.

In the Planning & Strategy phase, a custom roadmap is developed, outlining the steps needed to meet compliance standards. This involves selecting the appropriate security controls based on the organization’s needs and creating an implementation timeline to ensure that these controls are rolled out effectively.

The Implementation phase focuses on deploying the chosen security measures to safeguard systems and data. System hardening is performed to eliminate vulnerabilities, and policies and procedures are developed to guide security practices across the organization.

During the Validation & Testing phase, penetration testing is conducted to simulate real-world attacks and evaluate system resilience. Security controls are tested to ensure they are functioning as intended, followed by compliance verification to confirm adherence to required standards.
The Continuous Monitoring phase involves regular security audits to assess the system’s ongoing security health. Continuous assessments help identify any new vulnerabilities, while ongoing improvement efforts ensure that the organization’s security measures evolve with emerging threats.