Penetration testing, often called pen testing, is a controlled security assessment where expert ethical hackers simulate real-world cyber attacks on your systems, networks, and applications. Unlike automated scans, penetration testing involves active attempts to exploit vulnerabilities, revealing not just potential weaknesses but also demonstrating how attackers could chain multiple vulnerabilities to breach your defenses.
Think of it as hiring professional security experts to break into your digital infrastructure – they use the same tools and techniques as malicious hackers but do so safely and legally, providing detailed reports of their findings to help you strengthen your security.



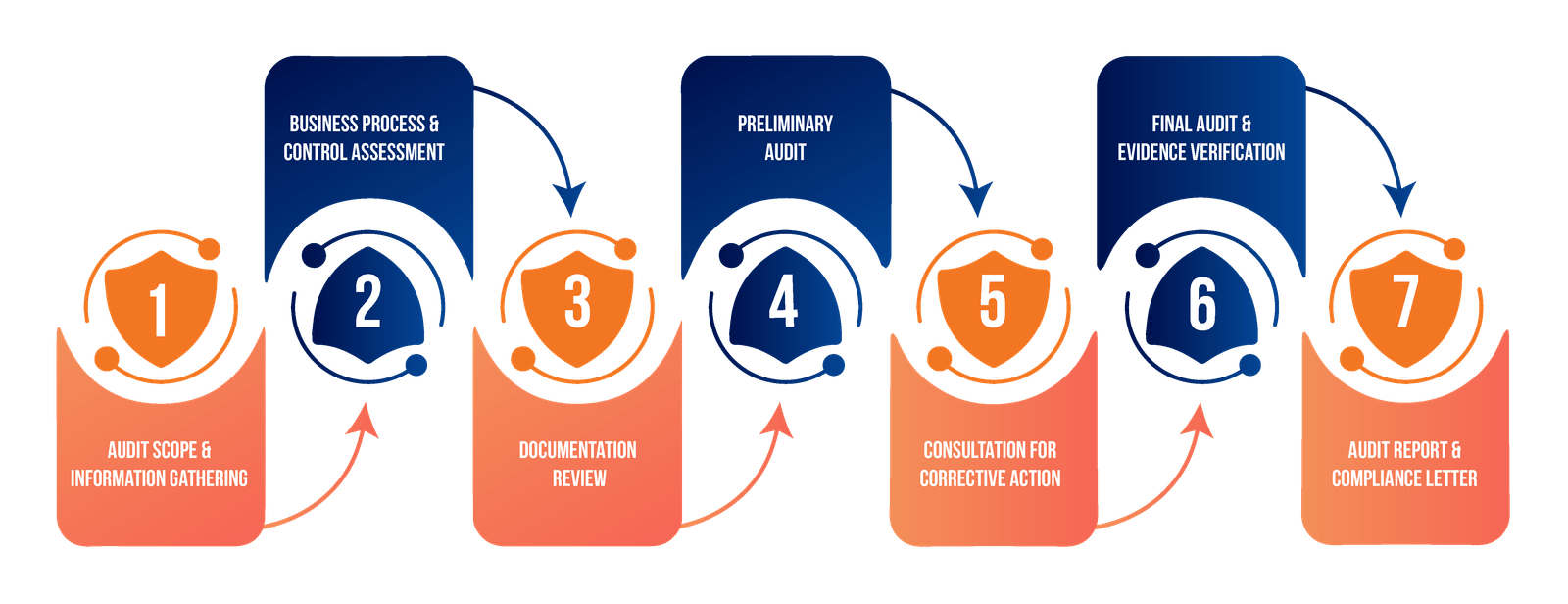
Define testing boundaries, objectives, and success criteria

Collect target system information and potential vulnerabilities

Identify security weaknesses through manual and automated methods

Safely attempt to exploit discovered vulnerabilities

Assess the potential impact of successful breaches

Deliver detailed findings and actionable recommendations
Guide your team in addressing discovered vulnerabilities

We maintain strict confidentiality protocols and sign comprehensive NDAs before beginning any engagement.
We offer both advisory services and implementation support, depending on your needs and preferences.
We establish clear KPIs at the project’s outset and provide regular progress reports against these metrics.
We’ll provide a preparation checklist, but typically you’ll need to: