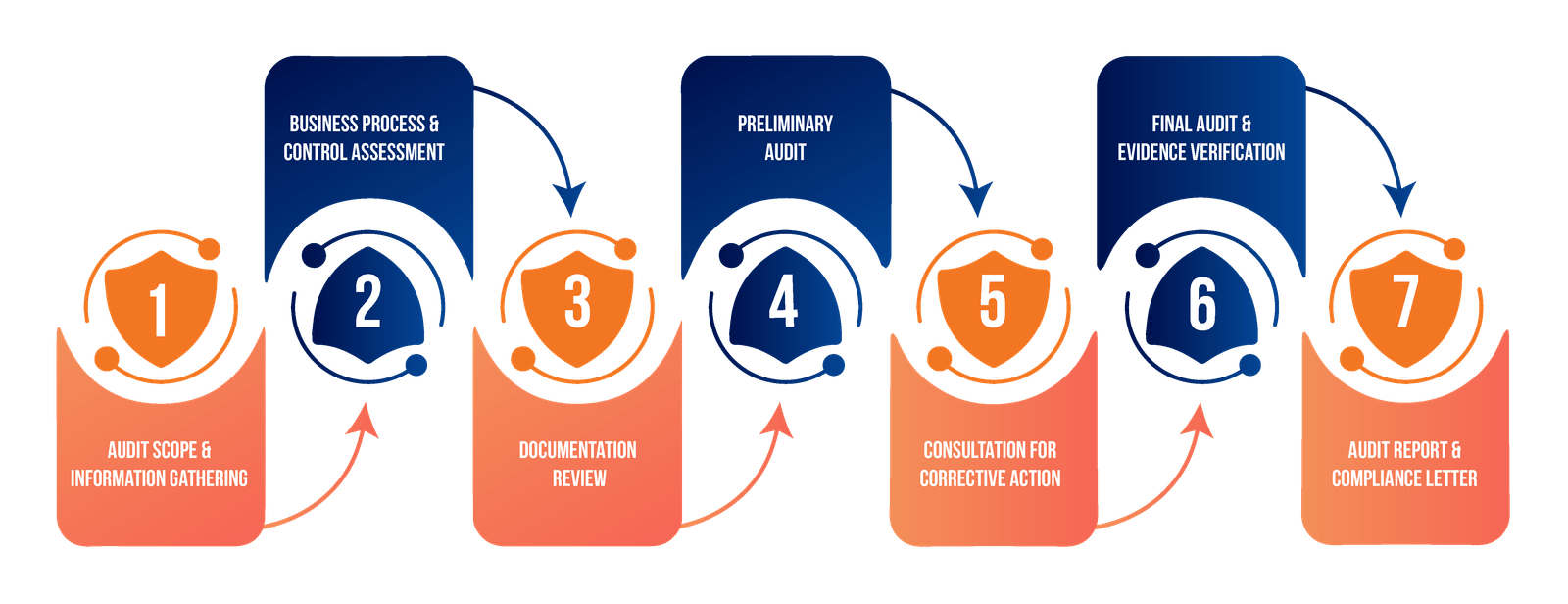
We begin by thoroughly analyzing your codebase and development requirements. Our team works with you to define review objectives and scope, then selects the most effective testing tools and methodologies based on your specific needs and technology stack.

Our senior developers perform detailed manual code inspections while leveraging automated scanning for vulnerability detection. We evaluate your architecture and design patterns against industry standards and conduct performance optimization analysis to identify potential improvements.

Every finding is documented with clear severity rankings and actionable remediation steps. We provide best practice implementation guidance and prepare an executive summary that communicates key findings and their business impact effectively.

Our partnership continues beyond the initial review. We verify remediation efforts, provide implementation assistance, and offer ongoing consultation to ensure sustained code quality improvement. Our team remains available to support your development journey.
From security vulnerabilities to performance optimization, we examine every aspect of your code
You’ll receive comprehensive reports including: