Wireless penetration testing is an authorized security assessment where our experts simulate malicious attacks on your wireless networks and access points to uncover exploitable vulnerabilities. Unlike basic automated scans, our specialists use the same advanced techniques as cyber criminals to thoroughly evaluate your wireless security posture.

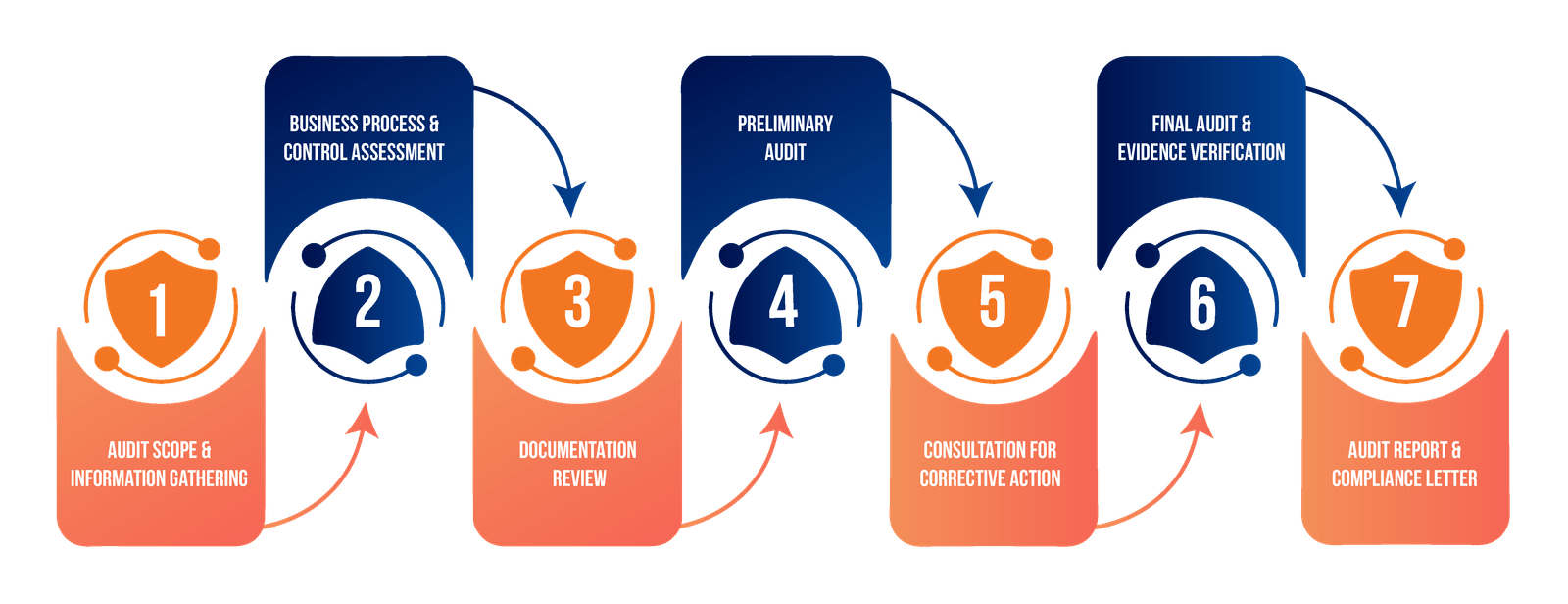
We map your wireless infrastructure, identify access points, and gather intelligence about your network architecture.

Our experts analyze encryption methods, authentication mechanisms, and network configurations for potential weaknesses.

We attempt controlled exploits to validate vulnerabilities and determine their real-world impact.

Our team documents findings assesses risks, and develops practical remediation strategies.

We deliver comprehensive reports and walk you through our findings and recommendations.

Modern businesses rely heavily on wireless connectivity, making WiFi networks an attractive target for cybercriminals. Regular testing helps protect sensitive data and maintain business continuity.


We can test all types of wireless networks including:
Our comprehensive reporting package includes:
We’ll need: